
New Dojo Intelligent IoT Vulnerability Scanner App Provides Consumers With Deep Insight Into The Cybersecurity Risks In Their Smart Homes
New Dojo Intelligent IoT Vulnerability Scanner App Provides Consumers With Deep Insight Into The Cybersecurity Risks In Their Smart Homes
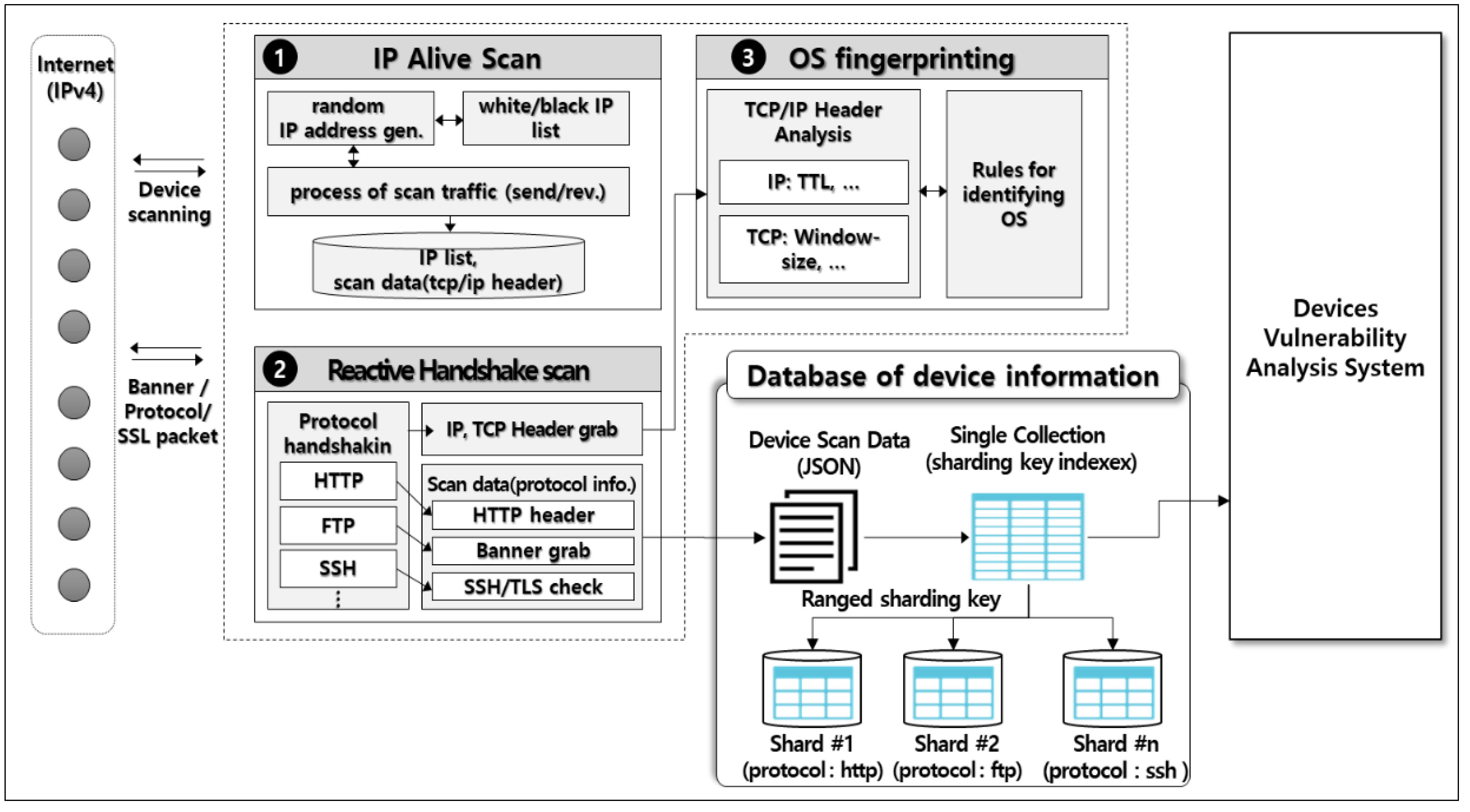
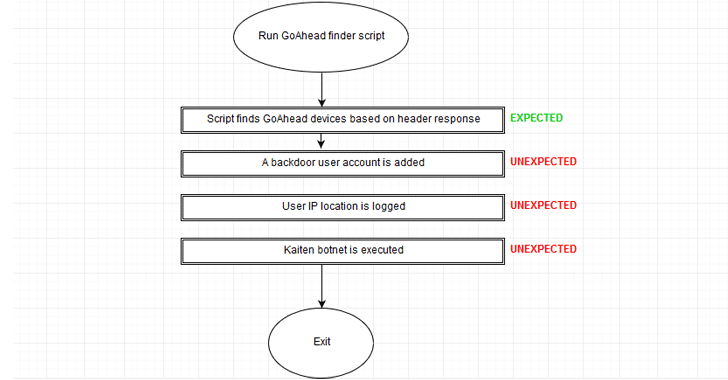

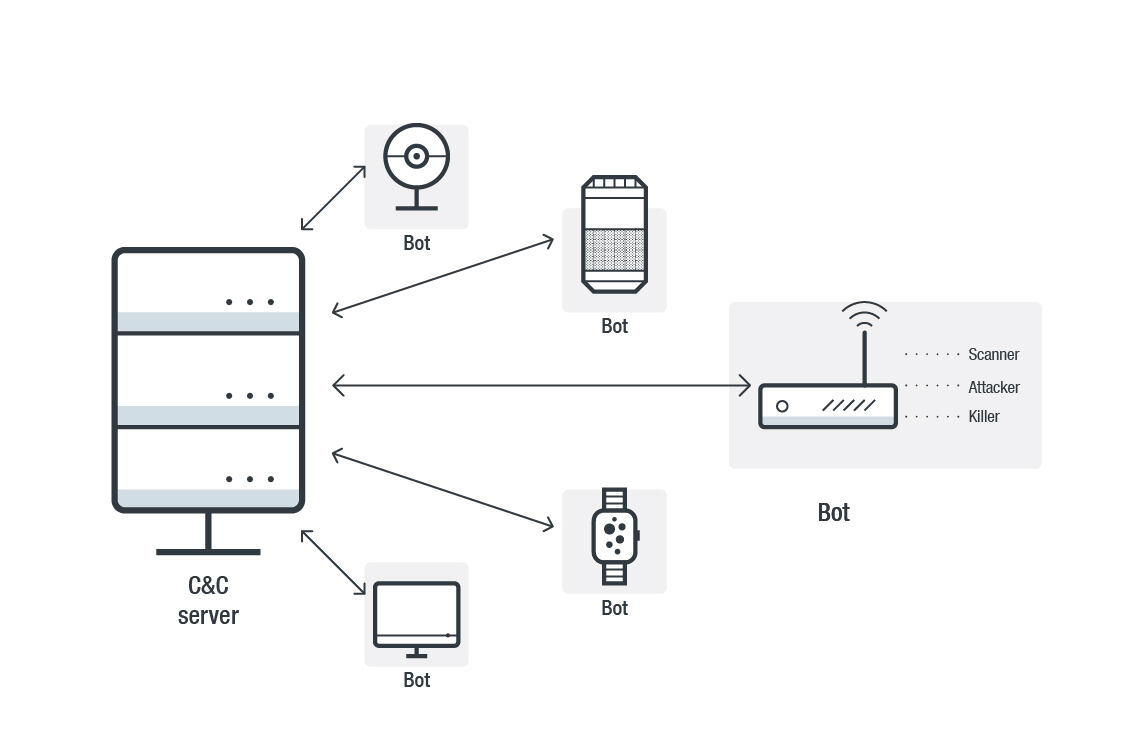
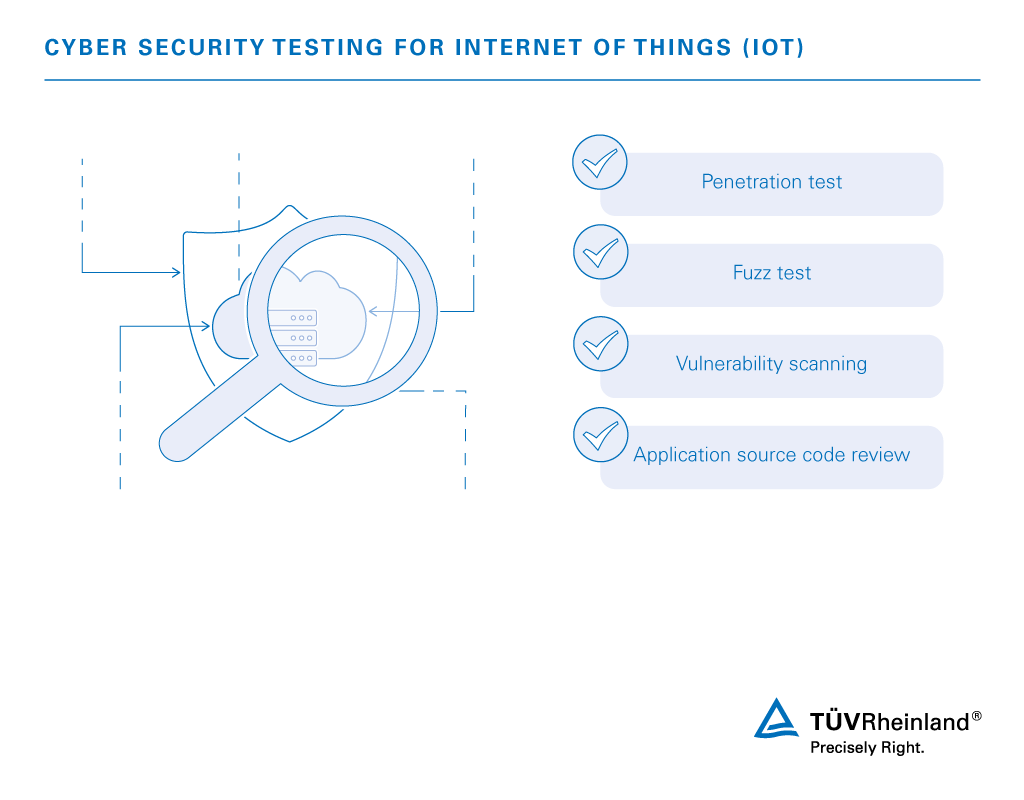

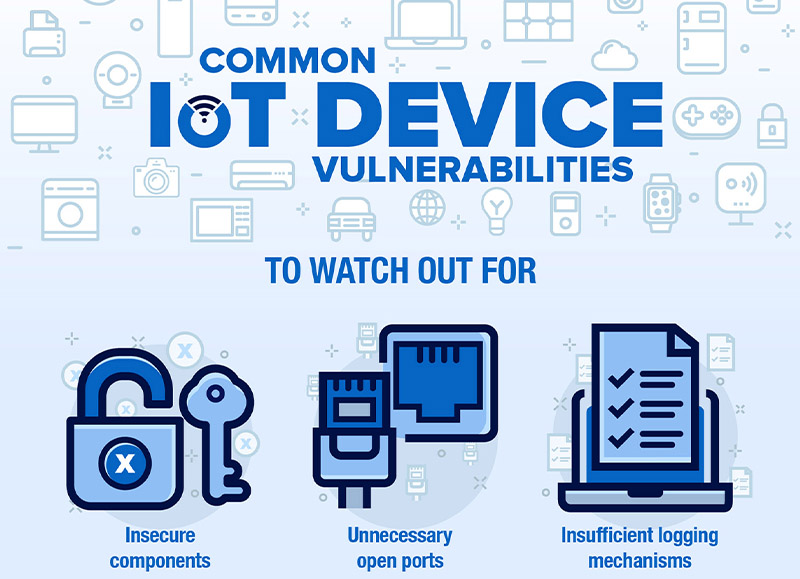


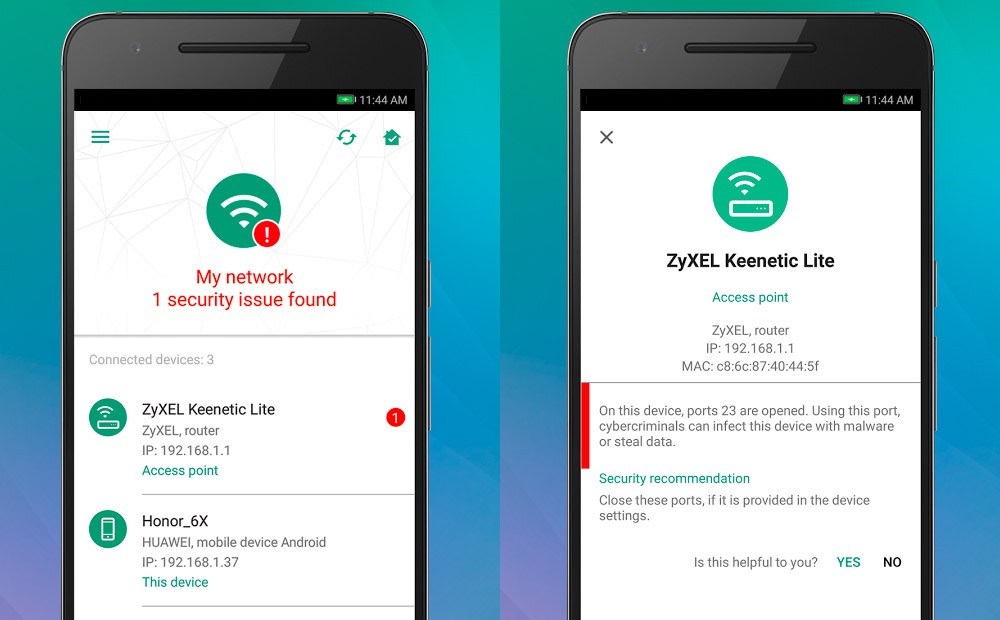


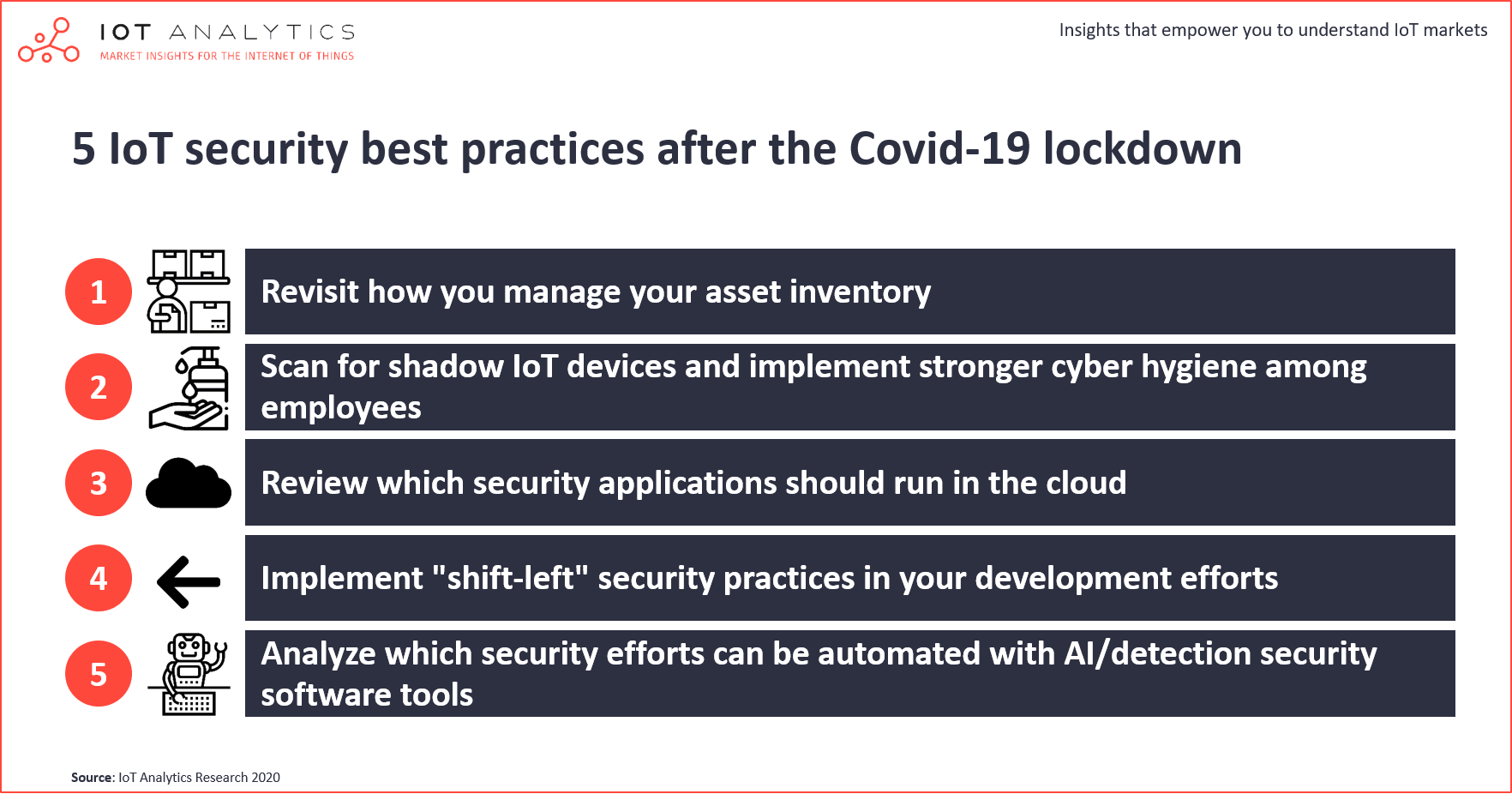

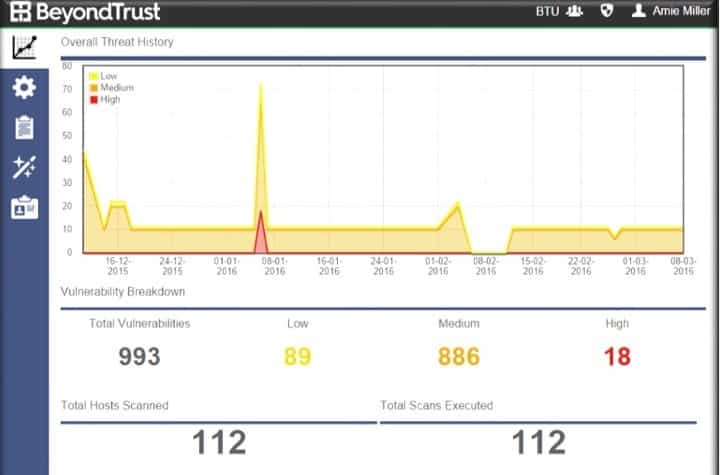

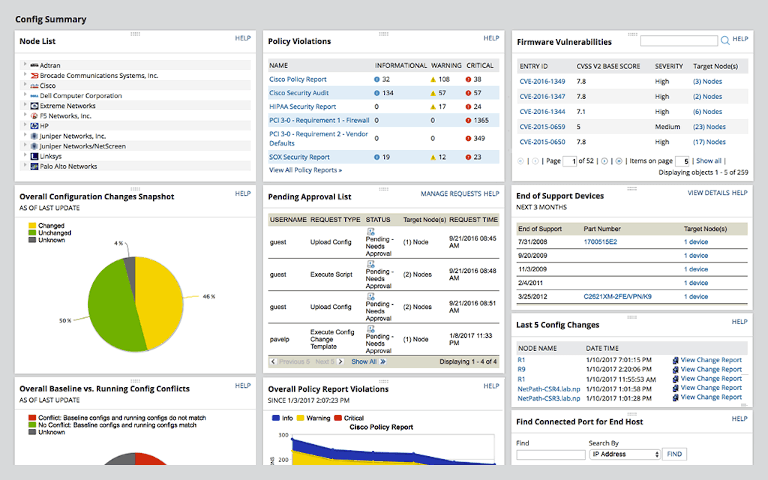
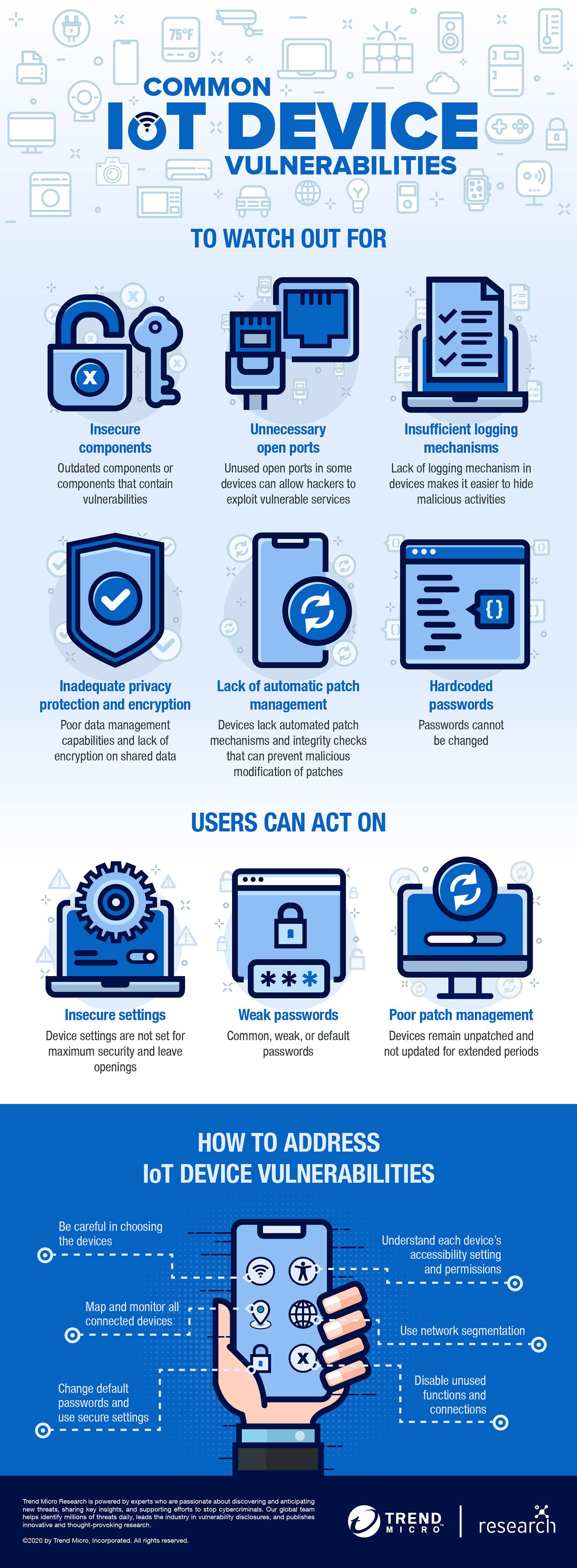
![Top 5 IoT vulnerability exploits in the smart home [list] Top 5 IoT vulnerability exploits in the smart home [list]](https://www.minim.com/hubfs/iot-vulns-feature-12.jpg)
